The CCISO certification is an industry-leading program that recognises the real-world experience necessary to succeed at the highest executive levels of information security. Bringing together all the components required for C-Level positions, the CCISO program combines audit management, governance, IS controls, human capital management, strategic program development and the financial expertise vital for leading a highly successful IS program. The CCISO Training Program can be the key to a successful transition to the highest ranks of information security management.
Target audience:
The CCISO program is for executives looking to hone their skills & learn to better align their information security programs to the goals of the organisation as well as aspiring CISOs. Other information security management certification programs focus on middle management. CCISO focuses on exposing middle managers to executive-level content as well as encouraging existing CISOs to continually improve their own processes & programs.
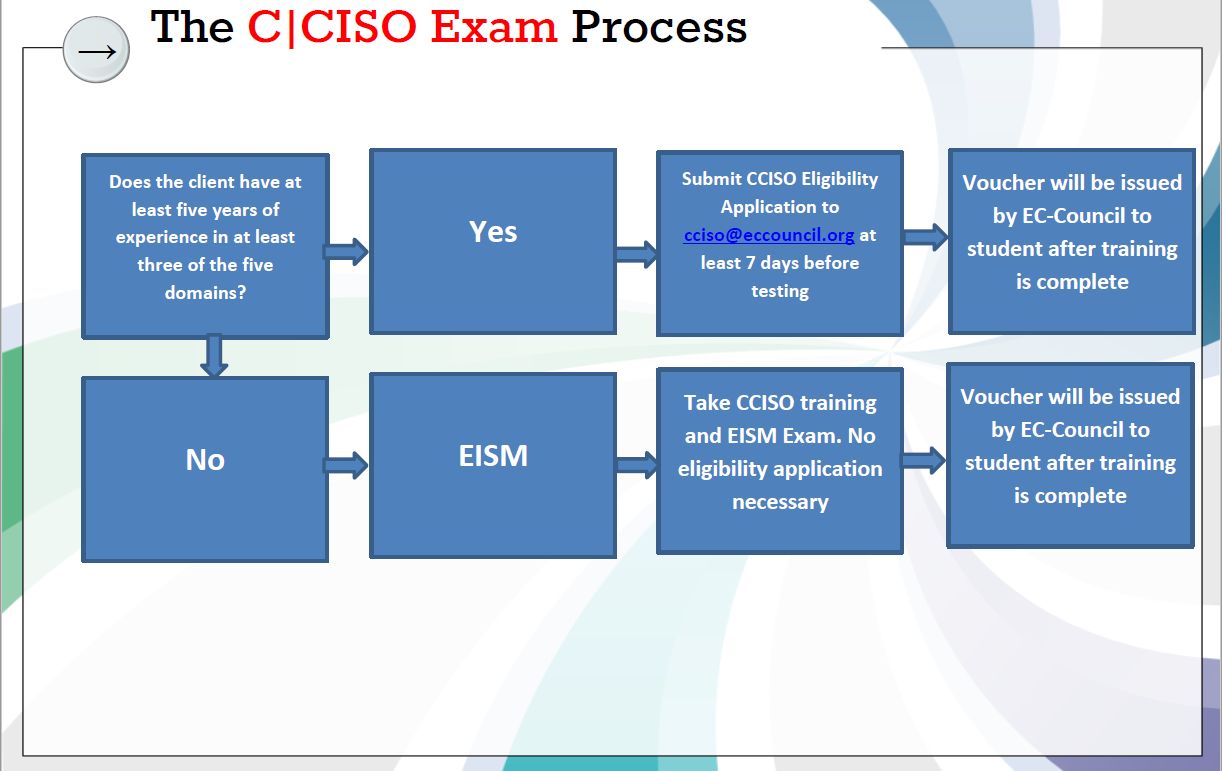
English knowledge and in order to sit for the CCISO exam, applicants attending the training must apply via the CCISO Eligibility Application, showing 5 years of experience in at least 3 of 5 CCISO domains (experience can be overlapping). Students who do not meet the eligibility criteria for the CCISO exam can sit for the EC-Council Information Security Manager (EISM) exam & apply for the CCISO exam once they meet the requirements.
EC Council is sourcing E-Learning training and certification partners globally for the iLearn Division. iLearn is EC-Council’s Official Training program, where a learner learns through instructor-led self-paced video-based training methodology. Self-paced in that a certification candidate can set its own learning pace by pausing the lectures and returning to their studies as their schedule permits.

THE ADVANTAGE OF iLEARN IS THAT IT HAS:
-
Step by step guide from EC Council’s Master trainers who teach virtual lessons through HD video
-
Rich content equivalent to our classroom training
-
Access iLabs, the virtual simulated lab with more than 140 lab exercises and 2200 hacking tools inbuilt in the system
-
A convenient 365-days access our training content on the web
-
A cost-effective solution to training without additional time investment.
THE iLEARN PACKAGE INCLUDES:
-
One Year Access to the E-courseware
-
Six months access to EC-Council's official Online lab environment (iLabs)
-
EC-Council’s Certification Exam Voucher (valid for one year)
-
One year access to EC-Council's expert instructor-led training modules with streaming video presentations for an all-inclusive training program that provides the benefits of classroom training at your own pace
iLearn online training is a distance learning program designed for those who cannot attend a live course. The program is for the people who have a very busy schedule and want to learn at their own pace through self-study.

KEY OUTCOMES:
-
Establishes the role of CISO and models for governance
-
Core concepts of information security controls, risk management, and compliance
-
Builds foundation for leadership through strategic planning, program management, and vendor management

CCISO is not a technical course but a leadership course designed specifically for experienced InfoSec professionals. The CCISO course covers the 5 CCISO Domain with deep dives into scenarios taken from the experience of the CISOs who contributed to the building of the Body of Knowledge, course, and exam.
COURSE OUTLINE:
DOMAIN 1 – GOVERNANCE
1.1. Information Program Security Management
1.2. Information Security Governance Program
1.3. Regulatory and Legal Compliance
1.4. Risk Management
DOMAIN 2 – RISK MANAGEMENT, CONTROLS, & AUDIT MANAGEMENT
1.1. Design, deploy, and manage security controls
1.2. Security control types and objectives
1.3. Implement control assurance frameworks
1.4. Audit management
DOMAIN 3 – SECURITY PROGRAM MANAGEMENT & OPERATIONS
1.1. The role of the CIS
1.2. Information Security Projects
DOMAIN 4 – IS CORE CONCEPTS
1.1. Access Controls
1.2. Physical Security
1.3. Disaster Recovery
1.4. Network Security
1.5. Threat and Vulnerability Management
1.6. Application Security
1.7. Encryption
DOMAIN 5 – STRATEGIC PLANNING, FINANCE, & VENDOR MANAGEMENT
1.1. Security Strategic Planning
1.2. Financial Planning

Exam Title: EC-Council Certified CISO
Exam Code: 712-50
Number of Questions: 150
Duration: 2.5 hours
Availability: ECC Exam Portal
Test Format: Scenario- based Multiple Choice
In order to sit for the CCISO exam, applicants attending the training must apply via the CCISO Eligibility Application, showing 5 years of experience in at least 3 of 5 CCISO domains (experience can be overlapping). Students who do not meet the eligibility criteria for the CCISO exam can sit for the EC-Council Information Security Manager (EISM) exam & apply for the CCISO exam once they meet the requirements.
The EC-Council group is made up of several entities that all help serve the same goal, which is to create a better, safer cyber-world through awareness and education.
Kérdésed van az e-learninggel kapcsolatban?
Ezek a tanfolyamok és e-learningek is érdekelhetnek
Tekintsd meg néhány további képzésünket a témában
EC-Council Certified Secure Computer User v2 (CSCU) E-learning and Exam

EC-Council Certified Network Defender (CND) E-learning and Exam

EC-Council Certified Ethical Hacker (CEH) v13 AI E-learning and Exam

EC-Council Computer Hacking Forensic Investigator (CHFI) E-learning and Exam

EC-Council Disaster Recovery Professional (EDRP) E-learning and Exam

EC-Council Certified Incident Handler v2 (ECIH) E-learning and Exam

Certified Application Security Engineer (CASE).NET E-learning and Exam

Certified Application Security Engineer (CASE) Java E-learning and Exam

Certified Threat Intelligence Analyst (C|TIA) E-learning and Exam

Certified Blockchain Professional (C|BP) E-learning and exam

EC-Council Certified SOC Analyst E-learning and Exam

EC-Council Certified Penetration Testing Professional (CPENT) E-learning and Exam

EC-Council Certified Web Application Hacking and Security Tester (WAHS) E-learning and Exam

EC-Council Ethical Hacking Core Skills E-learning and Exam

Certified Information Systems Auditor (CISA) vizsgafelkészítő e-learning

Certified Information Security Manager (CISM) vizsgafelkészítő e-learning

Certified Cloud Security Professional (CCSP) vizsgafelkészítő e-learning

Certified Information Systems Security Professional (CISSP) vizsgafelkészítő e-learning















A teljes tanfolyam hasznos volt.